CREDENTIAL LEAK MONITORING
Stay protected from leaked credentials and compromised databases with our advanced monitoring system. Get instant notifications about breaches and conduct confidential searches, ensuring the security of your valuable information. Stay one step ahead in safeguarding your credentials.

Features
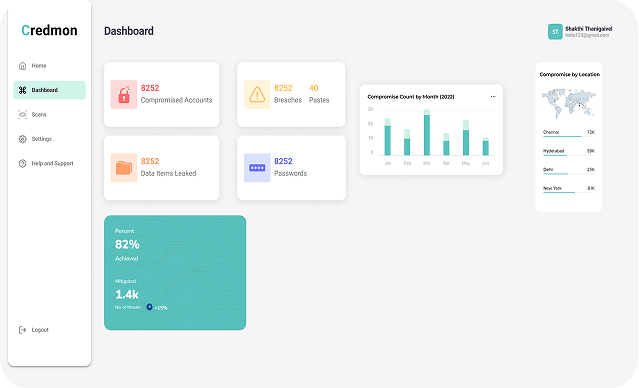
Credential Leak Monitoring
Our advanced credentials leak detection and monitoring system will tirelessly safeguard against leaked credentials and compromised databases. Stay one step ahead with prompt notifications, instantly alerting you to any personal or organizational credentials breach. Seamlessly conduct comprehensive searches, ensuring the utmost confidentiality of your valuable information.
Types of Credential Leaks
Password Breaches
Commonly occur when websites or services experience security breaches, resulting in leaked password databases.
Phishing Attacks
Social engineering techniques deceive users into disclosing their login credentials by posing as legitimate entities through emails, websites, or messages.
Keylogging and Malware
Malicious software, such as keyloggers, infects devices, capturing keystrokes and credentials entered by users.
How Credentials get leaked
Insider Threats
Employees can expose sensitive data via weak security practices like password sharing and phishing.
Data Breaches and Hacks
Attackers target databases, websites, or applications, exploiting vulnerabilities to gain unauthorized access and retrieve stored credentials.
Third-Party Compromises
Leaked credentials from one service can be used to compromise other accounts if users reuse passwords across multiple platforms.
How we help in minimizing the impact
Real-time Monitoring
Continuous scanning of sources to detect compromised credentials, providing alerts for proactive response.
Customized Notifications
Personalized notifications alert users when their specific credentials are found in leaked databases, enabling swift action and minimizing the window of vulnerability.
Severity Assessment
Evaluation of breach severity provides insights into the potential risks, allowing organizations to prioritize incident response and allocate resources effectively.