DARK WEB MONITORING
Protect your organization’s security with continuous dark web monitoring. Identify threats, data leaks, and credential breaches, safeguarding valuable assets through proactive threat detection and monitoring of company mentions and discussions.

Features
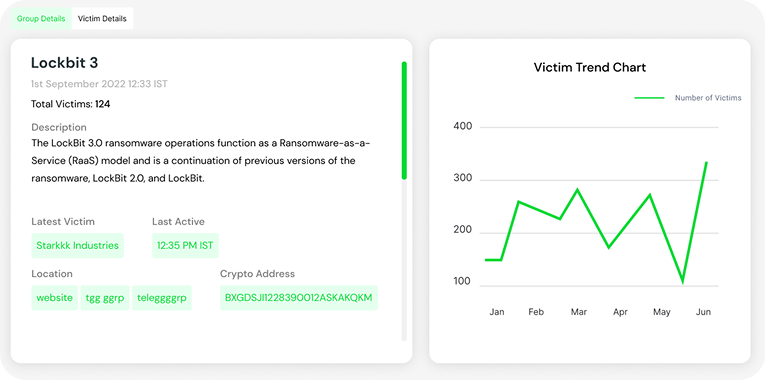
Dark Web Monitoring
Our advanced dark web monitoring solution continuously monitors the darkest corners of the internet, identifying company mentions, discussions, data leaks, credential breaches, and malware that pose risks to your organization’s security, helping you to protect your valuable assets with our proactive threat detection system.
Types of Threats
Sale of Stolen Data
The dark web provides a marketplace for buying and selling stolen data. Organizations may find their sensitive information, including login credentials, credit card details being traded or sold on these platforms.
Hacking Tools and Services
The dark web offers a range of hacking tools, exploit kits, and hacking services for threat actors to launch targeted attacks against organisations, exploit vulnerabilities, or gain unauthorised access.
Ransomware and Malware
The dark web hosts markets where malware and ransomware are bought and sold. Organizations can be exposed to these threats, potentially leading to the encryption of critical data, financial extortion.
Why should you monitor the dark web
Early Threat Detection
You can identify potential threats and attacks in early stages. This allows to take proactive measures to mitigate risks and prevent potential damage.
Data Breaches Prevention
Dark web monitoring enables organizations to identify if their sensitive data is being traded on illicit platforms. This allows them to take immediate action to protect the data and prevent data breaches.
Brand Protection
Monitoring the dark web helps organizations detect instances of brand impersonation and threat discussions, allowing them to promptly address these issues.
How we help in minimizing the impact
Company Mentions
The dark web hosts markets where malware and ransomware are bought and sold. Organizations can be exposed to these threats, potentially leading to the encryption of critical data, financial extortion.
Credential and Data Leak Monitoring
Comprehensive monitoring for data and credential leaks specific to your organization. Active search for any instances where your company’s sensitive data or user credentials are being shared on the dark web.
Deep Web Monitoring
Monitoring the deep web, which includes password-protected forums, private networks, and other restricted areas not indexed by search engines to ensure that organisations have visibility into a broader range of potential threats.