BOT THREAT MONITORING
Protect your digital assets with our intelligent, scalable, and cloud-based bot monitoring solution. Safeguard your websites, mobile apps, and APIs from automated attacks, while gaining valuable insights into global bot threats for optimal security.

Features
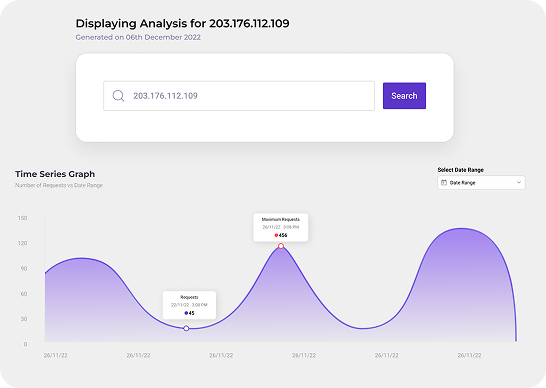
Bot Threat Monitoring
Our bot monitoring solution is intelligent, scalable and fully cloud-based bot management that protects your websites, mobile apps and API endpoints from automated attacks. It equips you with the latest threat intelligence of bots from all around the world to give you best-in-class insights.
Types of Bot Threats
Scalping Bots
Scalping bots target ticketing platforms or e-commerce websites, quickly purchasing popular items in bulk to resell at inflated prices. These bots exploit the limited availability of high-demand products, causing financial loss.
Botnet Attacks
Botnets consist of compromised devices infected with bots. Operators can launch massive DDoS attacks, overwhelming servers, and causing service disruptions or system inaccessibility.
Click Fraud Bots
Click fraud bots simulate legitimate clicks on online ads to fraudulently generate revenue or exhaust competitors’ advertising budgets. This type of bot activity deceives advertisers, reduces the effectiveness of campaigns, and distorts marketing analytics.
How do organisations get affected
Brand Reputation
Bot attacks can tarnish the reputation of a brand or organization. If bots are used to spam social media platforms or post fake reviews, it can erode trust and credibility among custome
Operational Disruption
Bot attacks can disrupt normal business operations. If a bot floods a website with spam traffic or executes resource-intensive activities, it can overload servers and cause performance issues.
Legal Conse
Malicious bots scrape data, exploit vulnerabilities, and cause breaches, compromising customer info, trade secrets, and valuable data.
How we help in minimizing the impact
Accurate Identification
Analyzing mouse tracking and activity can provide valuable insights into user behavior, allowing for accurate identification of bots. Bots often exhibit distinct patterns that differ from human users, enabling effective detection.
Reputation Preservation
Effective bot attack detection and mitigation safeguards brand reputation by preventing data breaches, spam, and fraud, ensuring customer trust, confidence, and long-term success.
Reduced False Positives
Utilizing mouse tracking and activity analysis minimizes false positives, as the system evaluates nuanced factors like cursor movement, click patterns, and scrolling behavior to accurately distinguish between legitimate users and bots, ensuring uninterrupted user experience.